Activate Cloud Shell
Cloud Shell is a virtual machine that is loaded with development tools. It offers a persistent 5GB home directory and runs on the Google Cloud. Cloud Shell provides command-line access to your Google Cloud resources.
- Click Activate Cloud Shell
at the top of the Google Cloud console.
When connected, you are already authenticated, and the project is set to your PROJECT_ID. The output contains a line that declares the PROJECT_ID for this session: Your Cloud Platform project in this session is set to YOUR_PROJECT_ID
gcloud is the command-line tool for Google Cloud. It comes pre-installed on Cloud Shell and supports tab completion.
- (Optional) You can list the active account name with this command:
gcloud auth list- Click Authorize.
- (Optional) You can list the project ID with this command:
gcloud config list projectOutput:[core] project = <project_ID>Task 1. Prepare the environment
First, you’ll prepare your deployment environment and download a sample application.
- Set the default Compute Engine zone to
<filled in at lab start>:
gcloud config set compute/zone- Clone the sample code:
git clone https://github.com/GoogleCloudPlatform/continuous-deployment-on-kubernetes.git- Navigate to the sample code directory:
cd continuous-deployment-on-kubernetesCreating a Kubernetes cluster
Now you’ll use the Kubernetes Engine to create and manage your Kubernetes cluster.
- Next, provision a Kubernetes cluster using Kubernetes Engine. This step can take several minutes to complete:
gcloud container clusters create jenkins-cd \ --num-nodes 2 \ --scopes "https://www.googleapis.com/auth/projecthosting,cloud-platform"The extra scopes enable Jenkins to access Cloud Source Repositories and Google Container Registry.
- Confirm that your cluster is running:
gcloud container clusters listExample Output:
Look for RUNNING in the STATUS column:NAME LOCATION MASTER_VERSION MASTER_IP MACHINE_TYPE NODE_VERSION NUM_NODES STATUS jenkins-cd 1.9.7-gke.3 35.237.126.84 e2-medium 1.9.7-gke.3 2 RUNNING
- Get the credentials for your cluster. Kubernetes Engine uses these credentials to access your newly provisioned cluster.
gcloud container clusters get-credentials jenkins-cd- Confirm that you can connect to your cluster:
kubectl cluster-infoExample output: If the cluster is running, the URLs of where your Kubernetes components are accessible display:
Kubernetes master is running at https://130.211.178.38 GLBCDefaultBackend is running at https://130.211.178.38/api/v1/proxy/namespaces/kube-system/services/default-http-backendHeapster is running at https://130.211.178.38/api/v1/proxy/namespaces/kube-system/services/heapster KubeDNS is running at https://130.211.178.38/api/v1/proxy/namespaces/kube-system/services/kube-dns kubernetes-dashboard is running at https://130.211.178.38/api/v1/proxy/namespaces/kube-system/services/kubernetes-dashboard
Task 2. Configure Helm
In this lab, you will use Helm to install Jenkins from the Charts repository. Helm is a package manager that makes it easy to configure and deploy Kubernetes applications. Your Cloud Shell will already have a recent, stable version of Helm pre-installed.
If curious, you can run helm version in Cloud Shell to check which version you are using and also ensure that Helm is installed.
- Add Helm’s
jenkinschart repository:
helm repo add jenkins https://charts.jenkins.io- Update the repo to ensure you get the latest list of charts:
helm repo updateTask 3. Configure and install Jenkins
You will use a custom values file to add the Google Cloud-specific plugin necessary to use service account credentials to reach your Cloud Source Repository.
- Use the Helm CLI to deploy the chart with your configuration set:
helm upgrade --install -f jenkins/values.yaml myjenkins jenkins/jenkins- Once that command completes ensure the Jenkins pod goes to the Running state and the container is in the READY state. This may take about 2 minutes:
kubectl get podsExample output: NAME READY STATUS RESTARTS AGE myjenkins-0 2/2 Running 0 1m
- Run the following command to setup port forwarding to the Jenkins UI from the Cloud Shell:
echo http://127.0.0.1:8080 kubectl --namespace default port-forward svc/myjenkins 8080:8080 >> /dev/null &- Now, check that the Jenkins Service was created properly:
kubectl get svcExample output: NAME CLUSTER-IP EXTERNAL-IP PORT(S) AGE myjenkins 10.35.249.67 8080/TCP 3h myjenkins-agent 10.35.248.1 50000/TCP 3h kubernetes 10.35.240.1 443/TCP 9h
We are using the Kubernetes Plugin so that our builder nodes will be automatically launched as necessary when the Jenkins master requests them. Upon completion of their work, they will automatically be turned down and their resources added back to the cluster’s resource pool.
Notice that this service exposes ports 8080 and 50000 for any pods that match the selector. This will expose the Jenkins web UI and builder/agent registration ports within the Kubernetes cluster.
Additionally, the jenkins-ui service is exposed using a ClusterIP so that it is not accessible from outside the cluster.
Task 4. Connect to Jenkins
- The Jenkins chart will automatically create an admin password for you. To retrieve it, run:
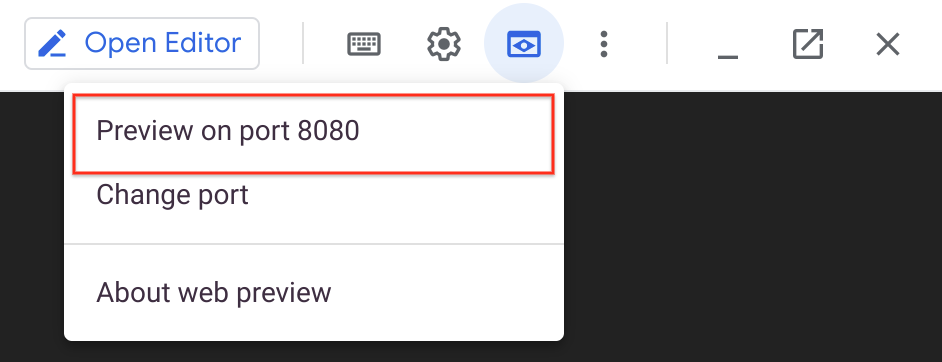
kubectl exec --namespace default -it svc/myjenkins -c jenkins -- /bin/cat /run/secrets/additional/chart-admin-password && echo- To get to the Jenkins user interface, click on the Web Preview button in cloud shell, then click Preview on port 8080:
- You should now be able to log in with the username
adminand your auto-generated password.
You may also be automatically logged in as well.
You now have Jenkins set up in your Kubernetes cluster!